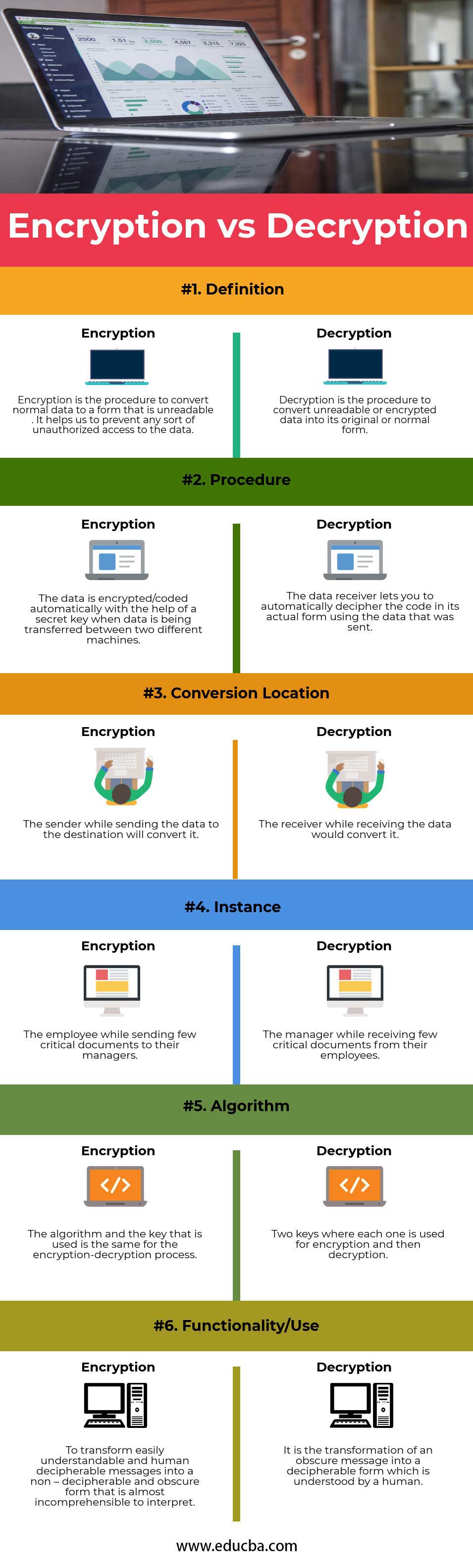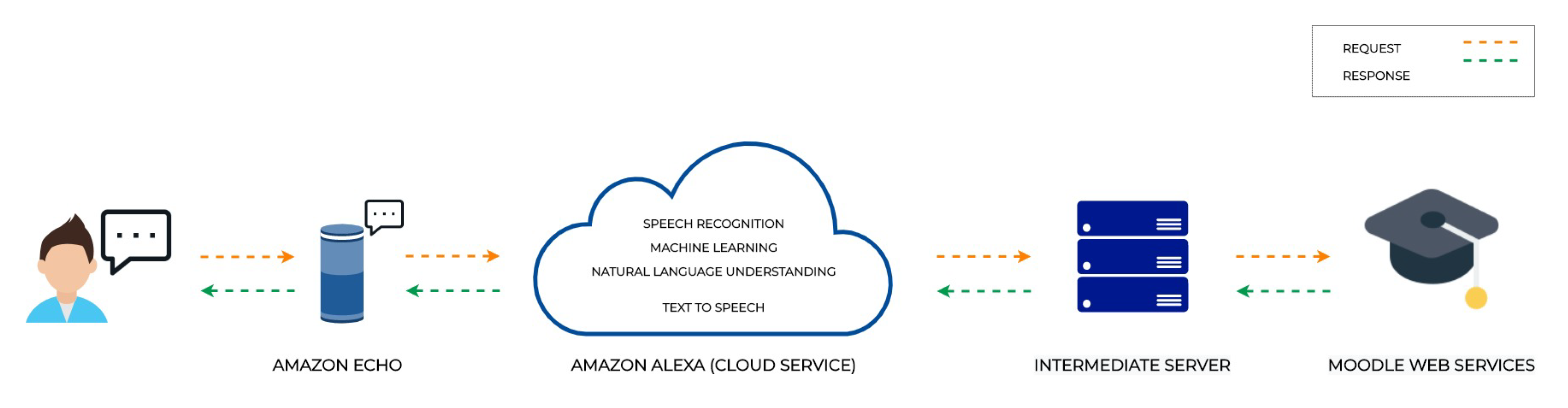
Applied Sciences | Free Full-Text | Moodle LMS Integration with Amazon Alexa: A Practical Experience | HTML

Amazon.com: Secret Window Cipher - Decoder Ring (Retroworks Decoder Ring Series #2) (Medium (USA 10)): Toys & Games

History of cryptography Encryption Cipher Code, fille, wood, code, substitution Cipher png | PNGWing