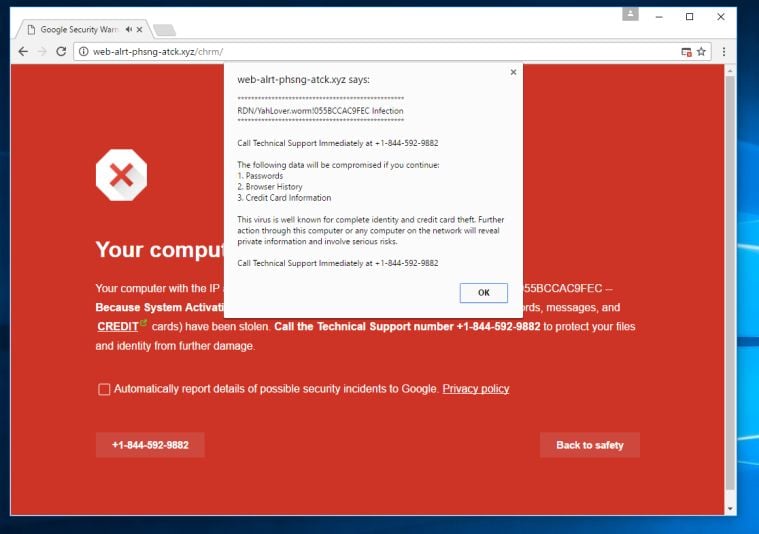
![PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man](https://thecybersecuritymancom.files.wordpress.com/2018/08/fake-ap-image.png?w=925)
PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man

How to create WiFi jammer and fake Access Point (AP) with NodeMCU (ESP8266) – Ehackify Cybersecurity Blog

Fingerprint Id Card Access Control Fingerprint Security Access Fake Fingerprint Detection Check In And Out Record Time - Fingerprint Recognition Device - AliExpress
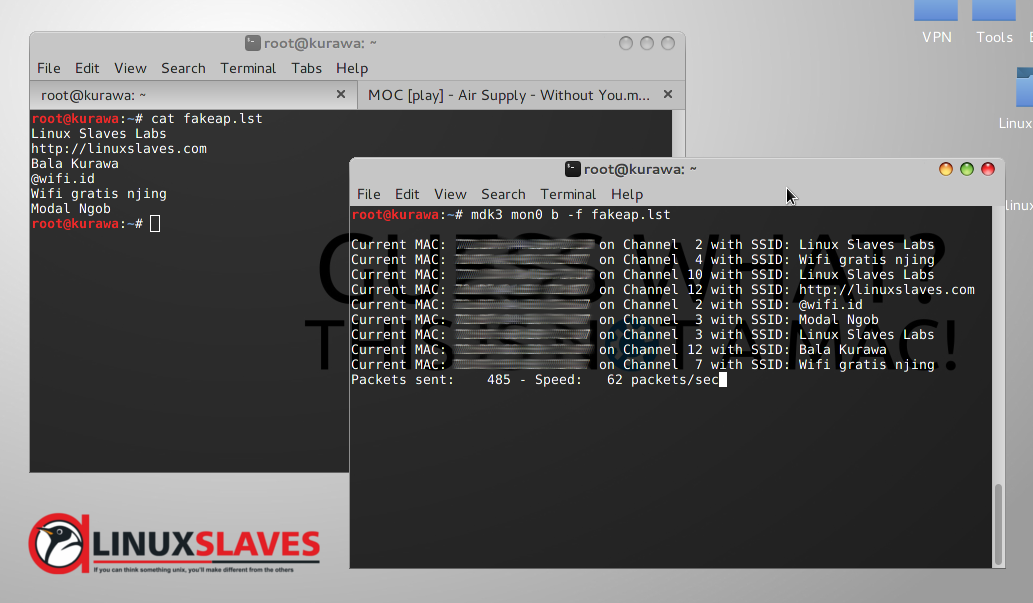
![PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man](https://thecybersecuritymancom.files.wordpress.com/2018/08/evil-twin.png?w=925)
PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man
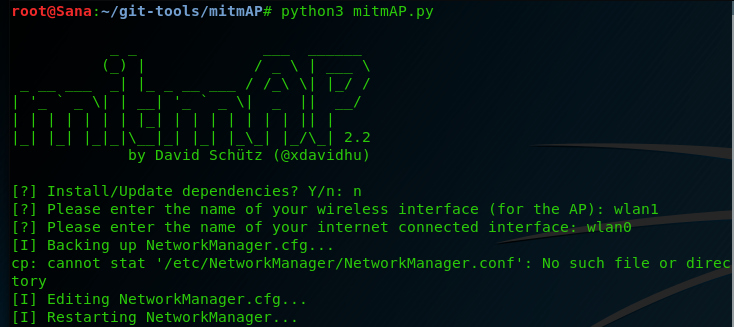
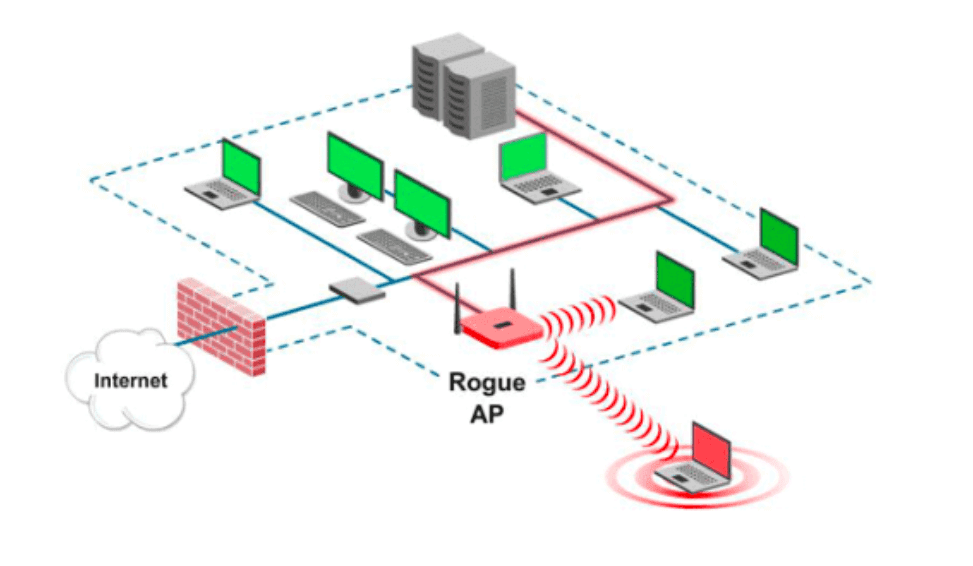
mitmAP - An Open Source Tool to Create a Fake Access Point and Sniff Data - Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses

Premium Vector | Car fake risk history online description report with warning vehicle access on computer laptop

This sounds SO fake but I swear it happened. I get access to the Casino for the first time ever and lose at CalicoKack for a bit, so I move to slots.