Smart Home Office Security Kit with NFC, RFID, Fingerprint Scanner, PIR and Ultrasonic Sensor – RAKwireless Store
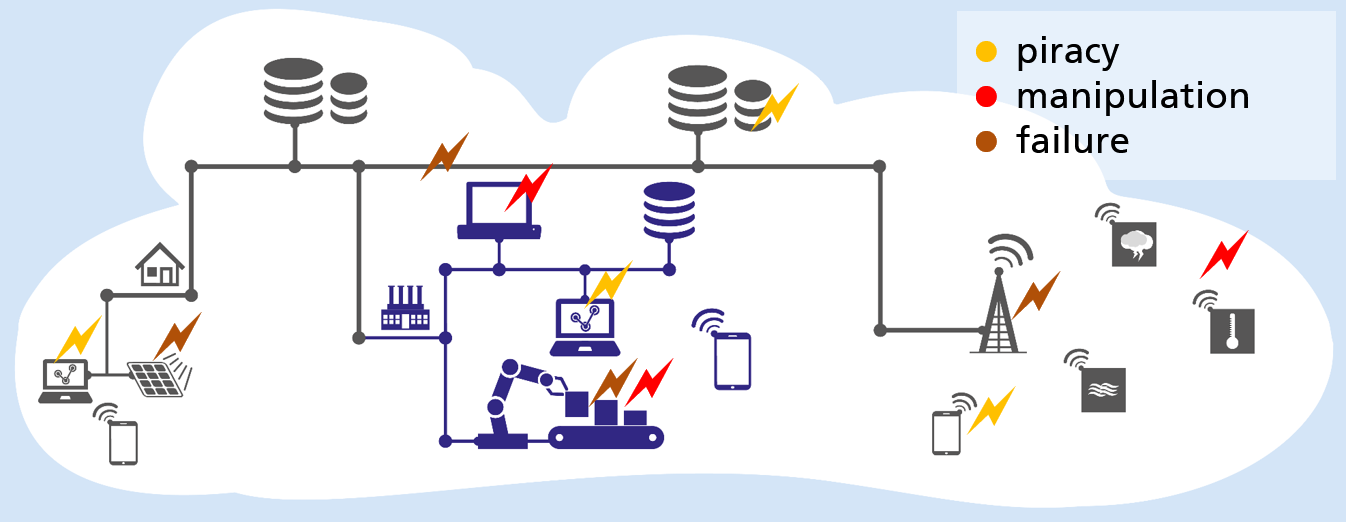
Sustainability | Free Full-Text | State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions

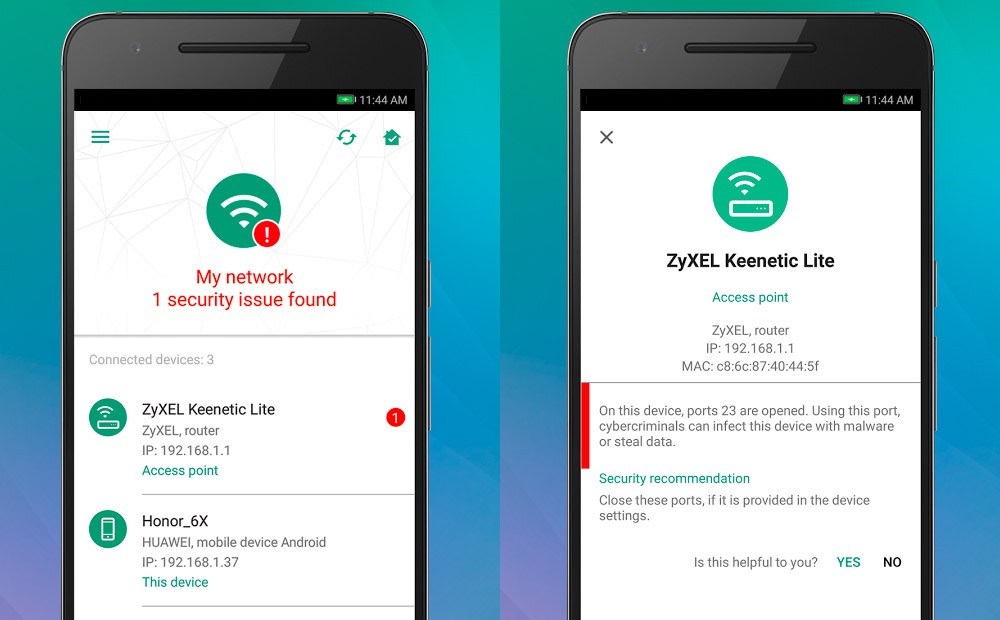
Check Point Software and Provision-ISR to provide on-device IoT security for video surveillance solutions – Intelligent CISO

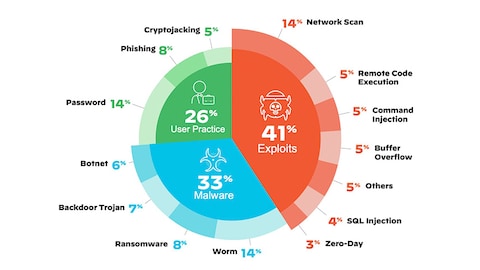
Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks