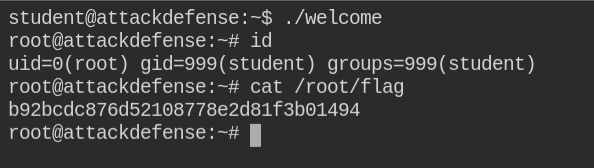
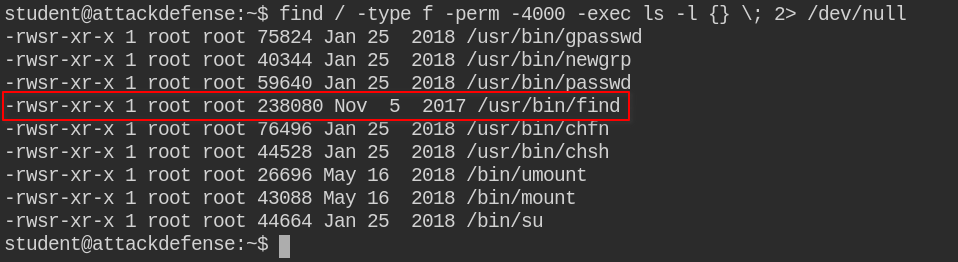
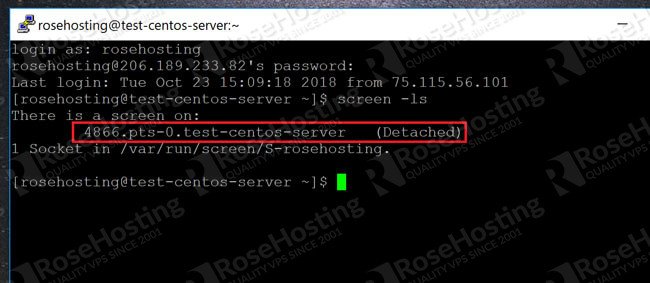
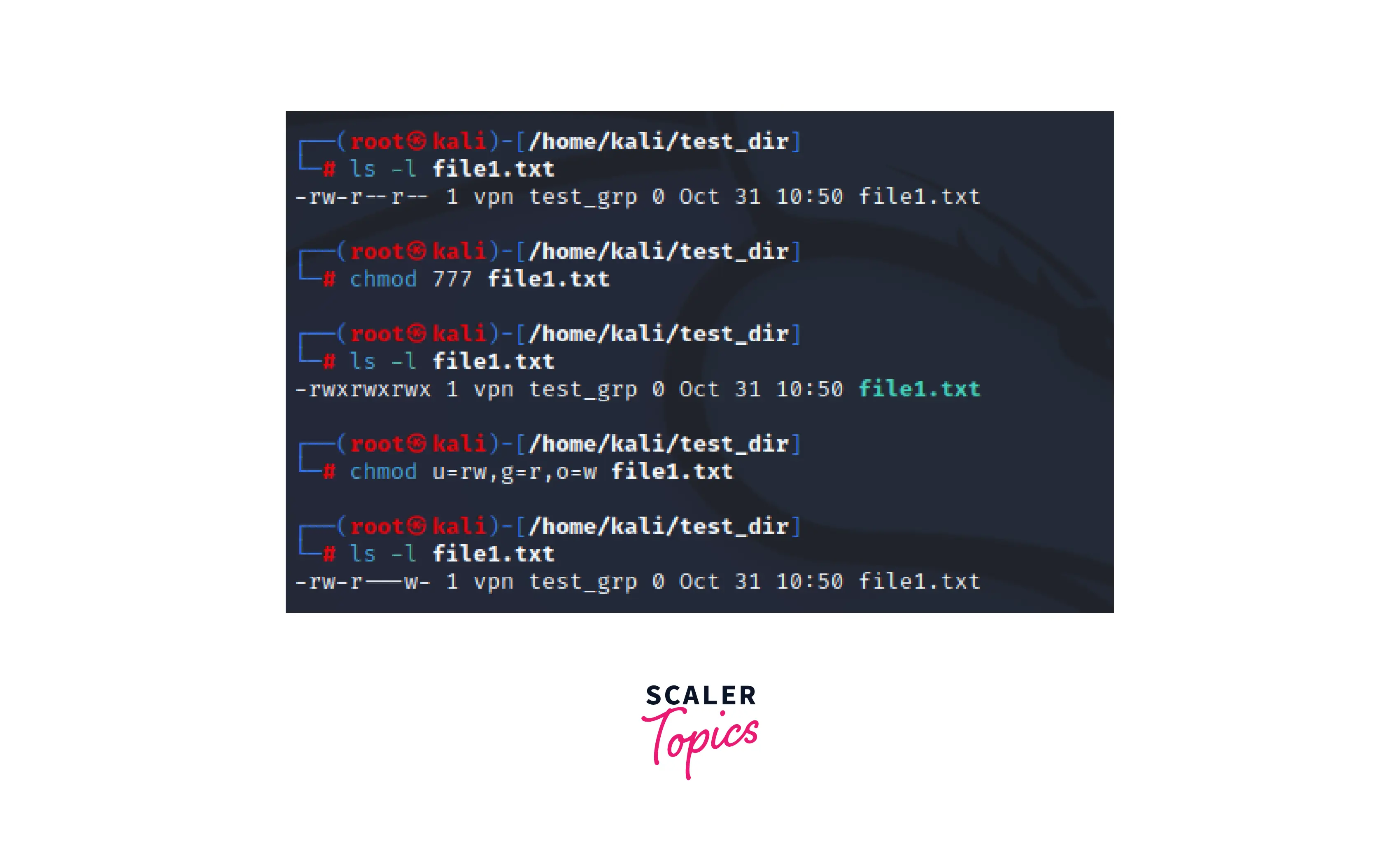
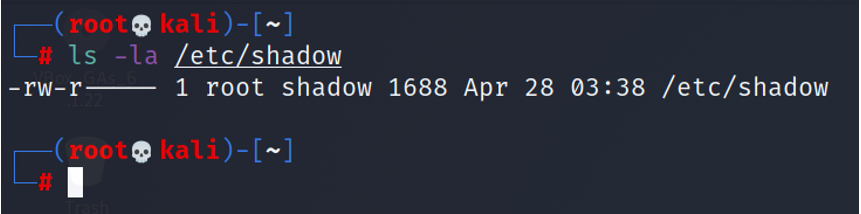
Why is the default file permission 666 in Linux? How is the security effect if the file becomes executable? - Quora
Why would using chmod 777 recursively from the root cause a Linux box to not boot? I could understand this if I were limiting permissions, but why would adding permissions cause this? -