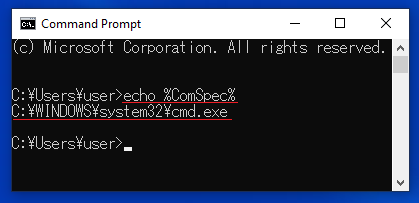
![Check Point Research on Twitter: "#Afrodita Ransomware, appears to be a new strain. Targeting businesses in Croatia via legitimate looking Excel spreadsheets. Subject: “Poziv na placanje” DZ: http://content-delivery[.]in/verynice.jpg XLSM ... Check Point Research on Twitter: "#Afrodita Ransomware, appears to be a new strain. Targeting businesses in Croatia via legitimate looking Excel spreadsheets. Subject: “Poziv na placanje” DZ: http://content-delivery[.]in/verynice.jpg XLSM ...](https://pbs.twimg.com/media/EK42UTgWwAAPoK7.jpg)
Check Point Research on Twitter: "#Afrodita Ransomware, appears to be a new strain. Targeting businesses in Croatia via legitimate looking Excel spreadsheets. Subject: “Poziv na placanje” DZ: http://content-delivery[.]in/verynice.jpg XLSM ...

Arkbird on Twitter: "As persistence push in HKEY_CURRENT_USER\Software\Classes\CLSID\{2DEA658F-54C1-4227-AF9B-260AB5FC3543}\InprocServer32 (who are the PlaySoundService InprocServer) for run the payload in appdata. https://t.co/XOtv5EKDHX https://t.co ...